IoT Projects
-
Mud crab traceability
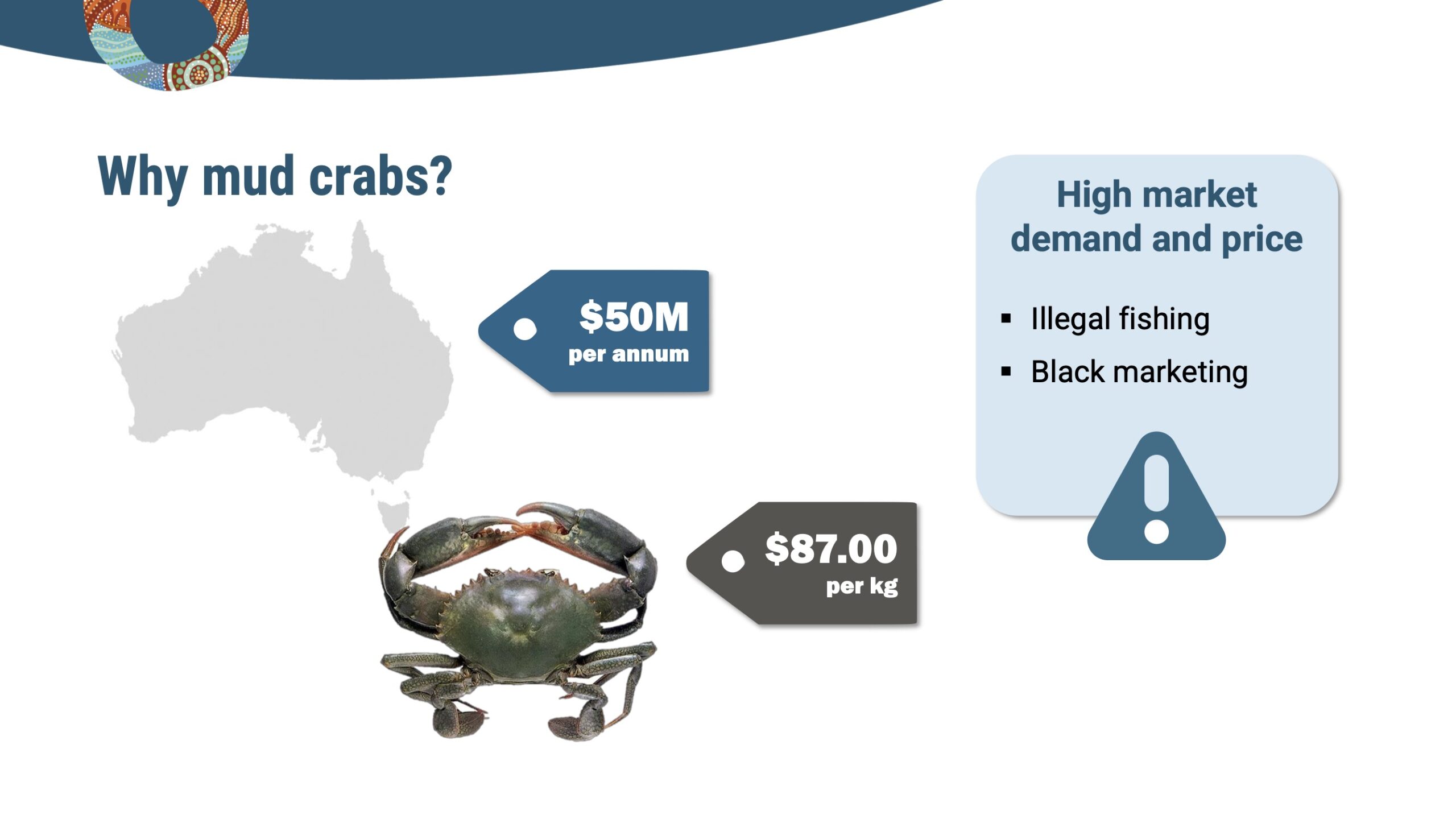
In the innovative Mud Crab Traceability Design project, IoT technologies such as QR codes are revolutionizing the seafood industry by enhancing traceability and sustainability. Each mud crab is tagged with a unique QR code that links to a webpage detailing its catch history and transport details, providing unprecedented transparency. This system not only builds consumer…
-
Circle 8 – Smart Bin

Circle8 smart bin is a joint development of UTS and CSIRO, commissioned by circle8, aiming to revolutionise plastic waste collection by making it easier, more widespread, and inclusive for citizens and entities to participate in the process.
-
Smart Bin for Federated Circular Economy

UTS Global Big Data Technologies Centre, in partnership with CSIRO, Australia’s national science agency, is developing AI powered Smart Bin Technologies to automatically classify and sort recycled bottles. This will help to produce high-quality recycled material and build Australia’s circular economy.
-
BeFAQT

Seafood auctions start from 5:30am every weekday at Sydney Fish Market, where buyers inspect the produce before their bidding. Sydney Fish Market had been planning to develop an online version of its famous seafood auction. The challenge then was how to provide the same onsite inspection experience (see, feel, and smell) to the online buyers.…
IoT Publications
-
[ELECTRONICS] GNN-Based Network Traffic Analysis for the Detection of Sequential Attacks in IoT
This research introduces a novel framework utilizing a sequential gated graph convolutional neural network (GGCN) designed specifically for botnet detection within Internet of Things (IoT) network environments. By capitalizing on the strengths of graph neural networks (GNNs) to represent network traffic as complex graph structures, our approach adeptly handles the temporal dynamics inherent to botnet…
-
[ComSec] NE-GConv: A lightweight node edge graph convolutional network for intrusion detection
Resource constraint devices are now the first choice of cyber criminals for launching cyberattacks. Network Intrusion Detection Systems (NIDS) play a critical role in the detection of cyberattacks. The latest Graph Neural Network (GNN) technology, which learns over graph-structured data and thus can capture the impact of the network, has shown profuse results in network…
-
[Globecom22] Leveraging Byte-Level Features for LSTM-based Anomaly Detection in Controller Area Networks
The legacy design of the Controller Area Network (CAN) weakens the encryption and authentication of the In-Vehicle Networks (IVN). Anomaly detection systems, e.g. the Long-Short Term Memory (LSTM) based Intrusion Detection System (IDS), are employed to remedy the defection of CAN. Existing works feed the LSTM-based IDS with the byte values of the data payload…
-
[RAID22] New Cloaking Region Obfuscation for Road Network-Indistinguishability and Location Privacy
The development of location-based services (LBS) leads to the rapid growth of location data, potentially increasing the threat to location privacy. Existing location obfuscation techniques focus on two-dimensional (2D) planar areas and overlook the features of road networks. In this paper, we leverage differential privacy and propose a new notion of Road Network-Indistinguishability (RN-Indistinguishability) to…
-
[OJ-CS] A Review on Security Issues and Solutions of the Internet of Drones
The Internet of Drones (IoD) has attracted increasing attention in recent years because of its portability and automation, and is being deployed in a wide range of fields (e.g., military, rescue and entertainment). Nevertheless, as a result of the inherently open nature of radio transmission paths in the IoD, data collected, generated or handled by…
-
[TITS] Personalized Location Privacy With Road Network-Indistinguishability
The proliferation of location-based services (LBS) leads to increasing concern about location privacy. Location obfuscation is a promising privacy-preserving technique but yet to be adequately tailored for vehicles in road networks. Existing obfuscation schemes are based primarily on the Euclidean distances and can lead to infeasible results, e.g., off-road locations. In this paper, we define…
-
[NSS19] A High-Performance Hybrid Blockchain System for Traceable IoT Applications
Blockchain, as an immutable distributed ledger, can be the key to realize secure and trustworthy IoT applications. However, existing blockchains can hardly achieve high-performance and high-security for large-scale IoT applications simultaneously. In this paper, we propose a hyper blockchain architecture combining the security of public blockchains with the efficiency of private blockchains. An IoT anchoring…
-
[Elsevier IoT] Capacity of blockchain based Internet-of-Things: Testbed and analysis
An integration of Internet-of-Things (IoT) and blockchain becomes increasingly important to secure IoT data in an anti-tampering manner. Challenges arise from the immense scale of IoT and the resultant impact of network partitioning on blockchain. We design a new testbed to evaluate the impact, where resource-limited IoT devices, acting as light nodes, are an integral…
-
[ComCom] Survey on blockchain for Internet of Things
The Internet of Things (IoT) is poised to transform human life and unleash enormous economic benefit. However, inadequate data security and trust of current IoT are seriously limiting its adoption. Blockchain, a distributed and tamper-resistant ledger, maintains consistent records of data at different locations, and has the potential to address the data security concern in…
-
[ISCIT17] Analytic model on data security in VANETs
Fast-changing topologies and uncoordinated transmissions are two critical challenges of implementing data security in vehicular ad-hoc networks (VANETs). We propose a new protocol, where transmitters adaptively switch between backing off retransmissions and changing keys to improve success rate. A new 3-dimensional (3-D) Markov model, which can analyze the proposed protocol with symmetric or asymmetric keys…
